Assigning NTFS Permissions and Special Permissions
You should follow certain guidelines for assigning NTFS permissions. Assign permissions according to group and user needs, which include allowing or preventing per. missions to be inherited from parent folders to subfolders and files that are contained in the parent folder.
How to Assign or Modify Permissions in Windows 10
Administrators, users with the Full Control permission, and owners of files and folders can assign permissions to user accounts and groups.
- Search the file or folder you want to modify.
- Right-click on it, and select Properties.
- Click in security tab to access the NTFS permissions.
- Click in Advanced button.
To assign or modify NTFS permissions for a file or a folder, in the Security tab of the Properties dialog box for the file or folder, configure the options that are shown next
Group Or User Names Allows you to select the user account or group for which you want to change permissions or that you want to remove from the list.
Permissions For group or user name Allows and denies permissions. Select the Allow check box to allow a or user name permission. Select the Deny check box to deny a permission.
clic edit to add o remove user o groups
Add Opens the Select Users Or Groups dialog box, which you use to select user accounts and groups to add to the Group Or User Names list
Remove Removes the selected user account or group and the associated permissions for the file or folder.
Advanced Opens the Advanced Security Settings dialog box for the selected folder so that you can grant or deny special permissions
Clicking the Add button on the Security tab of a file on folder’s properties dialog box display the Select Users or Groups dialog box Use this dialog box to add users or groups so that you can assign them permissions for accessing a folder or file.
How to Grant or Deny Special Permissions and and take ownership of files and folders
Click the Advanced button on the Security tab of a file or folder’s Properties dialog box to display the Advanced Security Settings dialog box, which lists the users and groups and the permissions they have on this object. The Permissions Entries box also shows where the permissions were inherited from and where they are apphed.
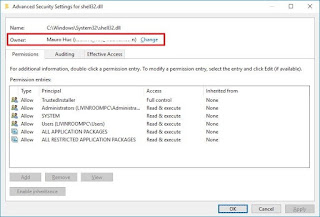
You can use the Advanced Security Settings dialog box to change the permissions set for a user or group. To change the permissions set for a user or group, On the "Advanced Security Settings" dialog box, you need to click the Change link, in the Owner's field.
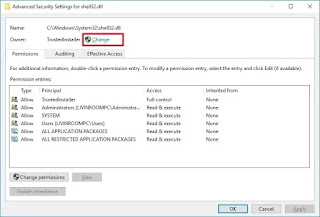
- Click the Advanced button.
- On the "Select User or Group" dialog box, click the Find Now button.
- In the search result, select your user account, and click OK.
s
Select This Object Type Allows you to select the types of objects you want to look for, such as built-in user accounts, groups, and computer accounts
From This Location Indicates where you are currently looking,for example in the domain or on the local computer.
Locations Allows you to select where you want to look, for example, in the domain or on the local computer.
From This Location Indicates where you are currently looking,for example in the domain or on the local computer.
Locations Allows you to select where you want to look, for example, in the domain or on the local computer.
Comun Queries Allows you to type in a list of built-in users or groups to be added.
Find Now Verifies the selected list of built-in users or groups to be added
- On the "Select User or Group" page, click OK.
- Click Apply.
- Click OK.

- Click OK again.
- Click OK one more time to complete this task.
When you grant permissions, grant users the minimum permissions that they need to get their job done. This is referred to as the principle of least privilege.
1
Taking Ownership of Files and Folders
Every object (file or folder) on an NTFS volume has an owner who controls how per. missions are set on the object and to whom permissions are granted. When a user creates an object, that user automatically becomes the object’s owner.
You can transfer ownership of files and folders from one user account or group to another. You can give someone the ability to take ownership and, as an administrator. You can take ownership of a file or folder. The following rules apply for taking ownership of a file or folder:
- The current owner or any user with Full Control permission can assign the Full Control standard permission or the Take Ownership special access permission to another user account or group, allowing the user account or any member of the group to take ownership.
- .An administrator can take ownership of a folder or file, regardless of assigned permissions. If an administrator takes ownership, the Administrators group becomes the owner, and any member of the Administrators group can change the permissions for the file or folder and assign the Take Ownership permission to another user account or group.
For example, if an employee leaves the company, an administrator can take ownership of the employee's files and assign the Take Ownership permission to another employee, and then that employee can take ownership of the former employee’s files.
You cannot assign anyone ownership of a file or folder. The owner of a file. an administrator, or anyone with Full Control permission can assign Take Ownership permission to a user account or group, allowing them to take ownership. To become the owner of a file or folder, a user or group member with Take Ownership permission must explicitly take ownership of the file or folder.
How to Prevent Permissions Inheritance
By default, subfolders and files inherit permissions that you assign to their m K folder. This is indicated in the Advanced Security Settings dialog box when the Inherit From Parent The Permission Entries That Apply To Child Objects check box is selected. To prevent a subfolder or file from inheriting permissions from a parent folder, clear the check box. You are then prompted to select one the options
Copy Copy the permission entries that were previously applied from the parent to ‘he child and then deny subsequent permissions inheritance from the parent folder.
Remove Remove the permission entries that were previously applied from the parent 10 the child and retain only the permissions that you explicitly assign here. Clicking this button removes all permissions from the file or folder; if you do not gram yourself permissions immediately afterward, you could lose access to the file. To recover access to the File, you would need to take ownership.
Cancel Cancel the dialog box.
Guidelines for Planning NTFS Permissions
If you take the time to plan your NTFS permissions and follow a few guidelines, you will find that permissions are more straightforward to manage than you might imagine.
Use the following guidelines when you assign NTFS permissions:
- To simplify administration, organize files into folders so that you can assign permissions to folders instead of directly to files.
- Allow u3ers only the level of access that they require. If a user only needs to read a file, assign the Read permission to his or her user account for the file. This reduces the possibility of users accidentally modifying or deleting important documents and application files.
- Create groups according to the access that the group members require for resources, and then assign the appropriate permissions to the group. Assign per' missions to individual user accounts only when necessary.
- When you assign permissions to application folders, assign the Read 8t Execute permission to the Users group and the Administrators group. This prevents application files from being accidentally deleted or damaged by users or viruses.
- When you assign permissions for public data folders, assign the Read & Execute‘ permission and the Write permission to the Users group and the Full Control permission to the CREATOR OWNER. By default, the user who creates a File is also owner of the File. The owner of a File can grant another user peritubslon to take ownership of the tile. This grants users the ability to read and modify documents that other users create (and the ability to read, modify, and delete the files and folders that they create.
- Do not make denying permissions a part of your permissions plan. Deny permissions only when it is essential to deny specific access to a specific user account of group.
- Encourage users to assign permissions to the files and folders that they create and teach them how to do so.
Managing Permissions Structures
The availability of so many different permissions often lures administrators into creating permission structures that are much more complicated than necessary. In addition to following the guidelines set out in this chapter (such as applying permissions to folders instead of files, and assigning permissions to groups instead of user accounts), you can make a permissions structure more manageable by doing
the following;
- For most companies, you will want to err on the side of being too secure. Make it a practice to lock everything down with permissions and then grant access only to those that need it. Also, grant only the level of permission that users need. It is often tempting to grant Full Control to users just to avoid complaints from those users about not being able to perform tasks, but avoid that temptation. On smaller networks, you might want to take an opposite approach-one in which you allow access to everything and then secure only those resources that need to be secured.
- Document your security decisions and encourage users to do so, as Well. You should record which folders and files have which permissions, and make notes on why you made the decision. Although it seems an extra burden (and does require more work upfront), this documentation is invaluable when the time comes to change or troubleshoot the permissions structure.


No comments:
Post a Comment